Security headers are a powerful way to strengthen SSL and to further secure the connection between site visitors and the webserver. Security Headers can be considered ‘instructions’ for the webbrowser. For example, the X-Frame-Options header will tell the browser if the page or site is allowed to be loaded in an iFrame.
We will discuss possible and recommended configurations for the four Recommended Security Headers within Really Simple SSL Pro:
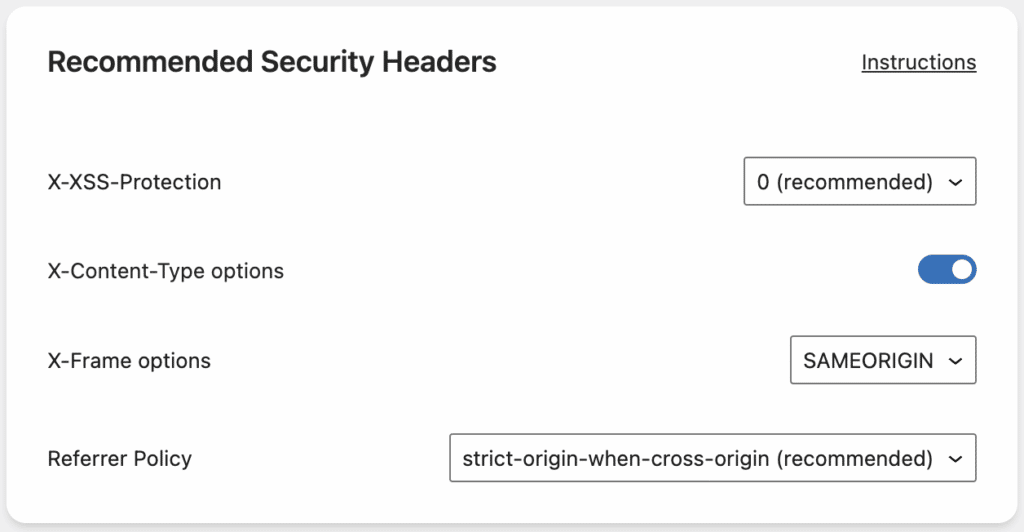
The Recommended Recurity Headers block within Really Simple SSL Pro
X-XSS-Protection
This header was used to manage Cross-site scripting protection within browsers. Older browsers had built-in XSS protection which filtered unsafe scripts. All major browsers have now removed their XSS protection and script filtering. With this header set to ‘0’, even older browsers will be instructed to disable XSS protection features, as they are known to introduce new possibilities for cross-site information leak attacks.
Recommended value: 0 (for all sites)
X-Content-Type options
This header protects site visitors against so-called ‘drive-by download attacks’, where malicious code may be ‘disguised’ as regular downloadable content.
Recommended value: allow (for all sites)
X-Frame options
This header will instruct the visitor’s browser whether to allow the site or page to be loaded into an iFrame. iFrames are commonly used as a method to let site vistors believe that they are on a website, while they are actually on a malicious site. This way, one could be tricked into entering sensitive information or clicking links.
This header should be set as strictly as possible. As most pagebuilders will load your site in an iFrame, entirely disabling iFrames will most likely break the editor of your pagebuilder. That is why the default value set by Really Simple SSL Pro is ‘SELF’.
Recommended value:
SAMEORIGIN (For sites using pagebuilders)
DENY (if you are not using pagebuilders, or using iFrames of your own site
ALLOW (if you are aware of an external site that needs to load the site into an iFrame)
Please note: If you set this header to ALLOW, we strongly recommend to specify the sites that are allowed to load the site within an iFrame, using the Content Security Policy Header
Referrer Policy
The Referrer Policy will instruct the browser which referrer information is included when navigating to another page or website. Referrer information consists the URL visited before the page the visitor is navigating to, including any possible parameters. Forwarding this information could be a security and privacy issue when forwarding to an insecure (HTTP) site, or when sensitive information is included into the parameters.
Recommended value:
strict-origin-when-cross-origin (only sends parameters within the own domain, and only sends the referring domain to external sites loading over HTTPS)
Depending on your configuration:
no-referrer-when-downgrade (relevant if you have included affiliate links on your site, that are utilizing parameters. They will only be sent when the external site is loaded over HTTPS.)
same-origin (if you only want referring pages and parameters exchanged within your site. Nothing is sent to external sites.)

