This article explains how to configure vulnerability detection in Really Simple SSL and what are important things to consider. If you want to know more about our latest release, also called 7.0 Vulnerabilities, read this article about our future endeavour’s for Really Simple SSL.
When you enable vulnerability detection and save settings, a pop-up will appear to configure your website and runs a first scan.

Notifications
You can configure when and how to show the notifications based on the minimum risk level. For example:
- Really Simple SSL Dashboard on Low-risk. This means the block progress on the dashboard of Really Simple SSL will be used to show a notification for ALL risk levels.
- Site-wide, admin notification on High-risk. This will show an admin notification for High-risk AND Critical vulnerabilities
- Email on Critical – You will only receive an email when a Critical vulnerability is found.
The test notifications are used to make sure everything works correctly so you’re notified accordingly. Emails are sent from your own server and when disabled, can be configured under Settings – General. If you do not receive an email, please check your server or use a plugin like WP Mail SMTP to make sure deliverability is 100%.
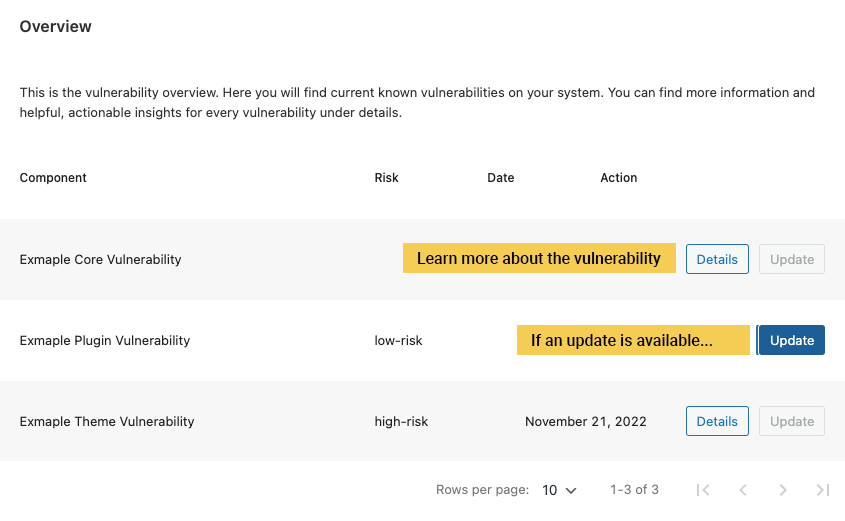
Components
This is an empty block, if you’re lucky. Here you will find information about present vulnerabilities, you can find details about the vulnerability itself, including possible actions.
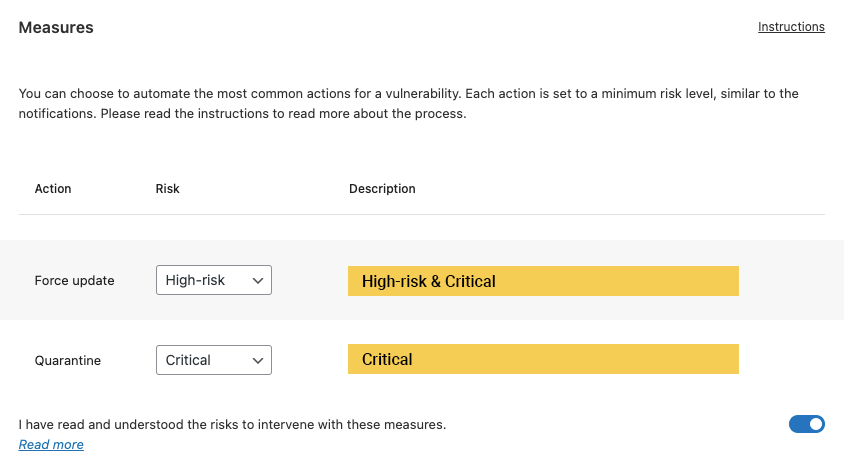
Measures
If you want peace of mind, you can use ‘Measures’. These are the most effective ways to keep your website from becoming vulnerable;
- Removing the vulnerability by update
- Removing the vulnerability by quarantine
This is what happens on below example;
In this example we have found a High-risk AND a Critical vulnerability. This has triggered the measures feature.
- You will receive an email about the vulnerabilities found. Ideally, you would take manual action, but holidays, time, and clients might get in the way. So we proceed;
- After 24 hours, an update will be forced (when available) on both vulnerabilities.
- It’s either successful, or we try again in another 24 hours. We will let you know.
- If another update round is unsuccessful, the Critical vulnerability will be escalated to Quarantine, and the High-risk vulnerability exits the process.
What happens now?
After communicating about the process to you we are ending the process with a final action.
High-risk vulnerability
The high-risk vulnerability was set to Force update. So either it updates or it doesn’t during the process. When an update is not available at the end of the process, you will be notified. In reality, plugins & themes that are actively developed will have an update with fix, before the vulnerability is publicized. A plugin author will be actively contacted approx two weeks before we end our update process. A plugin, theme etc that does not fix a vulnerability in 2 weeks is mostly like no longer active.
Critical vulnerability
Where the high-risk vulnerability ends the process, the critical vulnerability will enter quarantine and can no longer be executed. You will receive an email when done.
Quarantine means a full deactivation and obfuscation. It’s the most effective but will cause a disruption on your website. If it’s a plugin for calendar booking, it will no longer be available. If it’s a theme, the theme will be deactivated. In short, you will lose the functionality but safeguards the rest of the website. We recommend using actively developed plugins and themes, vulnerabilities are common, and fixes should also be common.

