There are many high quality plugins available on the WordPress Plugin Directory, offering a lot of flexibility to customize WordPress to your needs without having to write any code yourself.
However, installing third-party plugins and themes also means that you’re trusting code from another developer to run on your website. And since even the best developer could accidentally introduce a security vulnerability; it’s impossible to rule out the possibility of a vulnerability being discovered in a plugin/theme that you use on your website. Being informed about any vulnerabilities that are present on your site (and their level of severity) is the most important part, so that they can be addressed immediately.
Essential WordPress Security Practices
A secure foundation is your first line of defense against vulnerabilities. If the ‘main’ components of your site are insecure, even the most advanced security measures will only have limited effectiveness. Many security breaches occur due to the use of outdated software or vulnerable plugins. A properly maintained WordPress site that only uses carefully selected, up-to-date plugins is inherently more secure (and easier to protect).
Select your plugins (and themes) wisely
Prioritize plugins on the official WordPress.org Plugin Directory whenever possible. New plugins that are submitted to the WordPress.org Plugin Directory are reviewed by the Plugins Review Team before they can be downloaded, which provides you with some level of assurance that secure coding practices have been followed by plugin authors.
The WordPress.org Plugin Directory also lists detailed information about each plugin to help you determine if a plugin meets the standards that you require. Indicators such as the amount of Active installations, Last updated date, Recent reviews/ratings and the plugin’s Support Forum can help you make an informed decision about whether a plugin is trustworthy and suitable for your WordPress site.
In general, we recommend being selective before installing any plugins; and to limit the amount of plugins that you use on a website as much as possible. Not only will this reduce the likelihood of introducing vulnerabilities, it can also significantly improve your website’s performance/loading times.
Keep your software up-to-date
Keeping all components on your site updated is one of the most effective ways to stay ahead of vulnerabilities. Use the Vulnerability Scanning feature in Really Simple Security to quickly identify any vulnerable components on your website, so you can take precautionary measures right away.
We recommend enabling automatic updates for WordPress core, themes, and plugins whenever possible. In situations where automatic updates are not feasible on your environment, consider establishing a regular manual update schedule to ensure that all components on a site are kept up to date.
Don’t forget to update your PHP version to the latest supported release as well (or ask your Hosting Provider to do that for you), and avoid downgrading to outdated PHP version if a theme or plugin doesn’t support modern PHP versions. Outdated PHP versions no longer receive security patches and could expose you to unpatched security vulnerabilities.
Regularly audit your plugins, removing any that are no longer necessary or maintained
Periodically review your installed plugins to ensure that they all serve a current purpose on your site, and that they are still being maintained by their authors. Having abandoned or outdated plugins installed can result in unnecessary security risks.
Abandoned plugins are often a source of unpatched security issues, and while abandoned plugins are actively being removed from the WordPress.org Plugin Directory, it must be noted that such plugins are not deleted from your WordPress site if you have already installed them.
Vulnerability Scanning: An early warning system
The Vulnerability Scanning feature in Really Simple Security (located under SSL & Security -> Settings -> Vulnerabilities) is a powerful tool that helps you proactively identify and take action against any vulnerable components on your website. The plugin will run a daily scan to check for any vulnerabilities in your plugins, themes and WordPress core, to notify you about any issues that should be resolved as soon as possible.
Notifications can be configured based on the risk level of a detected vulnerability:

In the “Scan results” section, you will find detailed information about any vulnerabilities that are present in components on your environment: including the risk level (severity) of the vulnerability, a description of the vulnerability (by clicking the Details button) and any possible actions that can be taken.
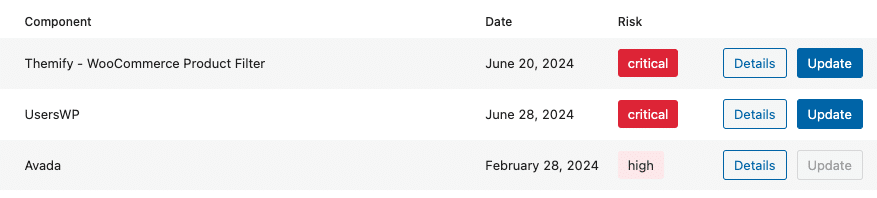
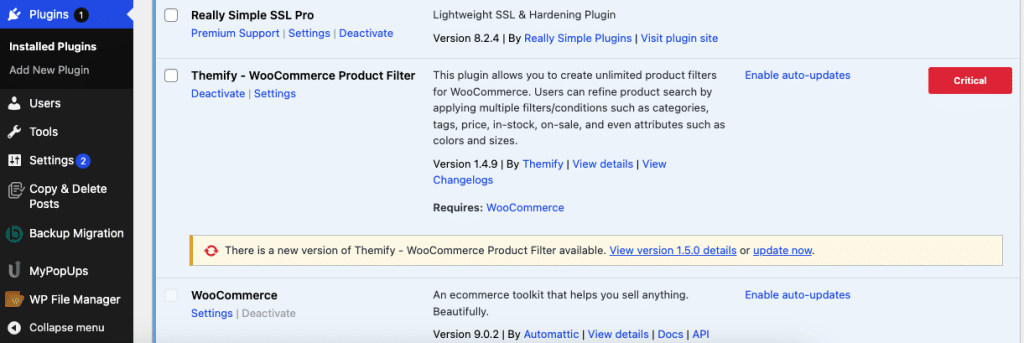
Enable the “Feedback in plugins overview” setting to directly insert vulnerability warnings and their severity in the Installed Plugins overview on your WordPress site (Plugins -> Installed Plugins).
Vulnerability Measures: Taking immediate action
The “Measures” functionality in the Pro plugin can be used to take action automatically based on the risk level of a detected vulnerability on your site. This could involve:
- Automatically updating components to a version where the vulnerability has been patched
- Quarantining vulnerable components (for instance; if a vulnerability poses a significant security risk, but no patch/update has been made available by its’ author yet; or when auto-updating did not succeed for any other reason)
When any vulnerabilities are detected in the scan, the Site Administrator will receive an email notification to inform them of this issue. After 24 hours, the system attempts to force-update the vulnerable components (provided that updates for these components are available).
If updating is unsuccessful, another update attempt is made (after another 24 hours). If it concerns a critical vulnerability, or if you configured Really Simple Security to quarantine plugins with a lower risk level than Critical, and the updates fail: the component is escalated to Quarantine.
Quarantining involves full deactivation and obfuscation of the vulnerable component, which is the most effective approach; but it may disrupt website functionality as it will result in the functionality of the quarantined component being disabled entirely. It is used as a last resort for critical vulnerabilities.
