The login page of your WordPress site is the gateway to your website’s back-end, which makes it an attractive target for a potential attacker to try gaining access to your site. Really Simple Security comes with a variety of settings that are specifically designed to protect User Accounts and the WordPress Login Page against various types of common threats.
In this article, we’ll explain how you can use the plugin to considerably improve the protection of User Accounts and the security of the WordPress Login Page.
Enable Two-Factor Authentication (2FA)
It is highly recommended to enable Two-Factor Authentication (2FA) for accounts on your WordPress website (Settings -> Login Protection -> Two-step Verification). This will require an additional “factor” besides just entering the username and password of an Account in order to successfully log in to the site.
This means that even if an attacker manages to obtain the password of an Account on your website; they would still require the ‘second factor’ before they can log in to the Account. Really Simple Security offers two 2FA methods, and you can select which 2FA methods are available for each “user role” on your site.
We recommend requiring Administrators to use TOTP (authenticator apps, e.g. Google Authenticator) as their 2FA method, because this method generates the 2FA codes on a separate device.
Email verification: A verification code is sent to the user’s email address.
- Pros: easy to use, no need to install additional apps
- Cons: if the user’s e-mail address is compromised, attackers could intercept the verification code
TOTP/Authenticator app: Verification with time-based one-time passwords (TOTP) generated with authenticator apps, like Google Authenticator.
- Pros: improves security due to verification codes being generated on a separate device
- Cons: installation of an authenticator app required, risk of losing access to the device with the authenticator app
Detailed instructions on how to set-up Two-Factor Authentication (2FA) are available here: https://really-simple-ssl.com/instructions/two-factor-authentication/
Password Security
By default, WordPress contains a Password Strength meter which is displayed when configuring a new password for your Account. The problem is that users can decide to override this check by simply ticking the “Confirm use of weak password” checkbox, and they would still be able to configure an insufficiently strong password. Enabling the “Enforce strong passwords” setting (located under Login protection -> Password security) in Really Simple Security disables the possibility for users to configure a weak password when registering an account, or when changing their password.
However, one of the most significant risks that impact the security of accounts on your WordPress website involves the use of passwords that had previously been compromised in data breaches. This could allow for credential stuffing attacks, whereby a hacker tries previously breached usernames and passwords to gain access to an account.
To counter these types of attacks, it is recommended to activate the “Compromised password check” option to check if compromised credentials are being entered during account creation (or modification). It verifies whether a supplied password has previously appeared in any data breaches by cross-referencing it with the Have I Been Pwned database, and prevents the account from being created if it concerns a previously breached password.
Finally, we recommend combining these settings with “Enforce frequent password change” to enforce frequent password changes for all users, or only for selected user roles (e.g. Administrators). This should be done to ensure that all accounts on your WordPress site have sufficiently strong passwords configured. Users that have to change their password will receive an email to inform them that their password will expire in 7 days. When the user resets their password, they will now be required to select a password that meets the new Password Strength requirements.
Managing User Sessions
After you’ve successfully logged in to your WordPress site, you will receive valid session/authentication cookies. These cookies allow you to access the site without having to enter your login credentials again (until the session expires).
However, if these session cookies are somehow obtained by an attacker, that would allow them to perform a “session hijacking/cookie stealing” attack. In this scenario, an attacker that manages to obtain a user’s session cookies (for example, this could be done through malware on the user’s local device, or by intercepting insecure public network traffic) can impersonate that user. The attacker can insert these stolen authentication cookies into their own browser session to gain unauthorized access to the user’s account, and their access would persist until the session expires.
By default, WordPress keeps users logged in for extended periods: 48 hours by default, and 14 days (!) if the “Remember Me” checkbox had been enabled on the login page. Really Simple Security allows you to shorten this duration to 8 hours, reducing the window of opportunity for an attacker to use stolen authentication cookies to their advantage (Settings -> Login protection -> Password security).
We highly recommend combining the “Limit logged in session duration” feature with the setting to “Disable the Remember Me checkbox” from the login page, as enabling the Remember Me option would result in the validity of the session being extended to 14 days, regardless of your configuration for the “Limit logged in session duration” setting.
Limit Login Attempts
Certain types of attacks on the login page (such as Brute Force or Credential Stuffing attacks) involve repeatedly attempting to log in with different password combinations. For increased protection against these types of attacks, you can enable the Limit Login Attempts functionality in Really Simple Security (“Settings -> Login Protection -> Limit Login Attempts”), which automatically blocks IP addresses/usernames that exceed the acceptable amount of failed login attempts within a certain timeframe.
Limit Login Attempts additionally provides you with an Event Log that records all activity on the login page, allowing you to quickly identify and take action against potentially malicious traffic.
Please also see our dedicated article about Limit Login Attempts for a detailed explanation on how to enable and configure this: https://really-simple-ssl.com/instructions/limit-login-attempts/
Blocking Login Attempts from specific locations (Geo-blocking)
If your site only expects to receive Login Attempts from users in certain countries, you can use the Regions section under Limit Login Attempts to block login attempts that originate from any other countries. This adds an additional layer of security by preventing unauthorized attempts from locations where your legitimate users are unlikely to be located.
No countries are blocked by default. To block specific countries (or entire continents) from using the login page on your site, navigate to the “Settings -> Login Protection -> Limit Login Attempts” tab and scroll down to the “Regions” section.
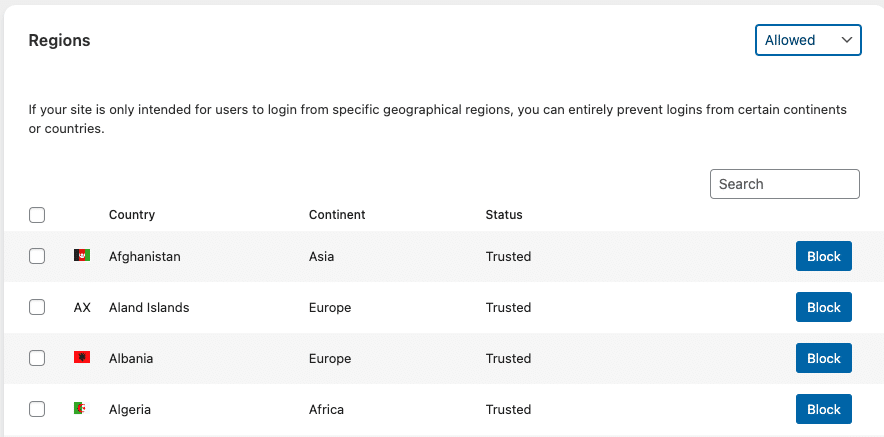
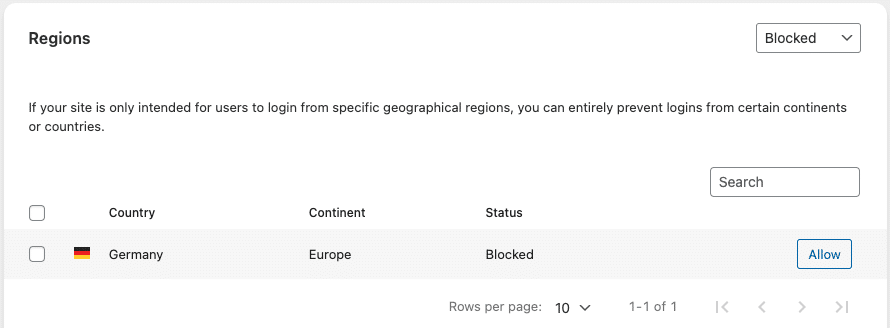
Change the filter in the dropdown menu to “Allowed” or “Continents” to view a list of available countries, where you can select countries (or entire continents) that you want to block from using your login page. In the below example, we’ve configured a block on Login Attempts originating from Germany.
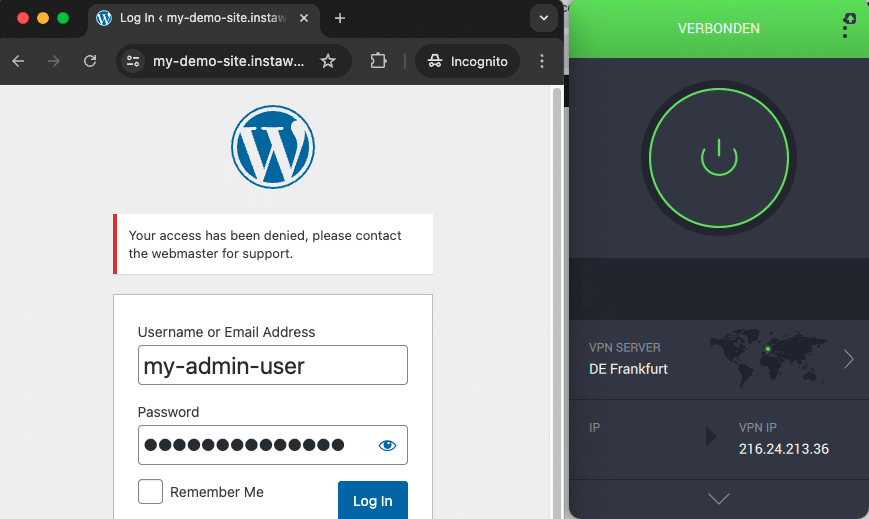
As a result, the following message appears when trying to submit login attempts from a German IP address.
Prevent Login Feedback
WordPress default login feedback can inadvertently help attackers by confirming whether they have correctly ‘guessed’ the username of an existing account on your WordPress site.
That feedback allows an attacker to test whether a user account exists by submitting repeated login attempts with various usernames. This is possible because WordPress informs them when they’ve entered a correct username (but with an invalid password), but displays a different message if that user does not exist on the site at all.
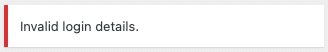
You can disable the default login feedback to prevent malicious actors from being able to use this information to their advantage. Enabling the “Prevent login feedback” setting (under SSL & Security -> Settings -> Hardening -> Basic) disables the default WordPress login feedback, and replaces it with generic messages that do not reveal any account information:
Custom Login URL
This feature allows you to change the location of your default WordPress login page (/wp-admin/, wp-login.php) to an URL of your choosing, which adds another layer of security through obscurity by making it harder for a potential attacker to locate your login page. This setting is located under SSL & Security -> Settings -> Hardening -> Advanced.
Enabling a Custom Login URL will redirect anyone trying to access the ‘standard’ login URL to another page on your site (you can configure which page that should be). The default behavior is to redirect to the 404 Not Found page, which can be seen in the example video below:
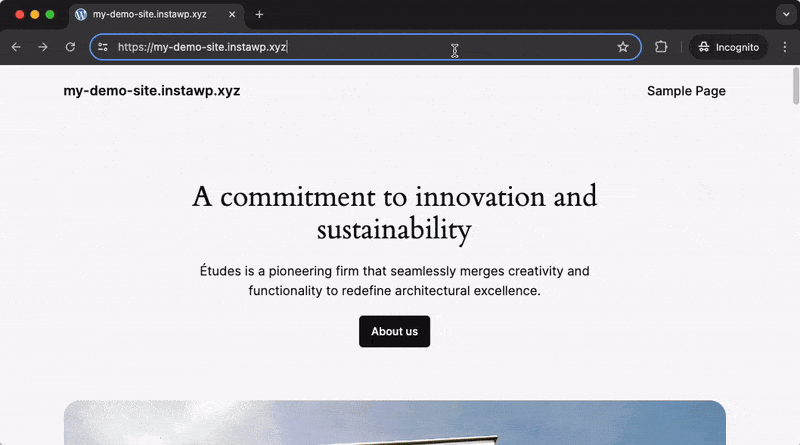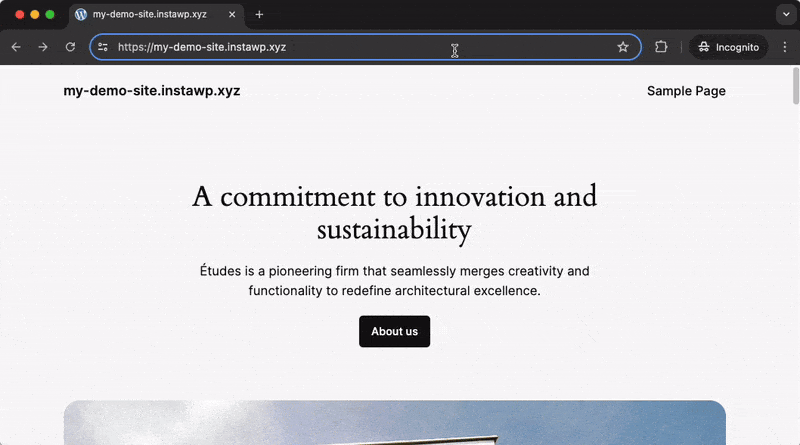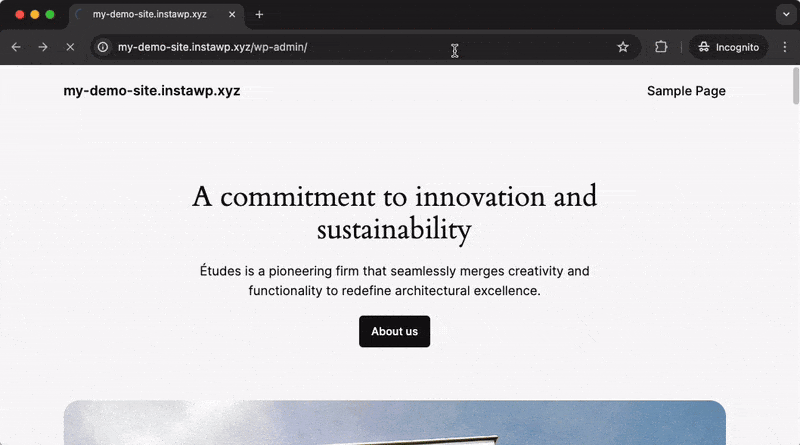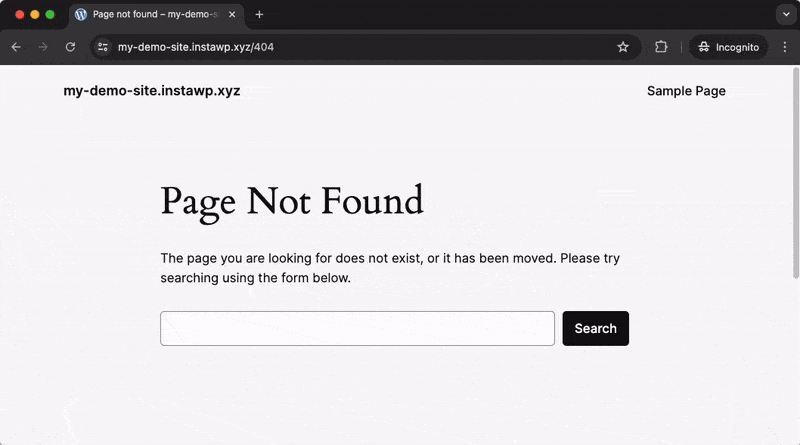
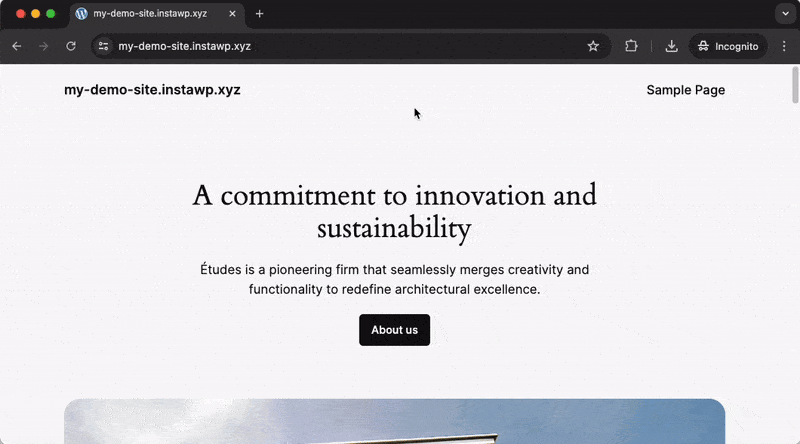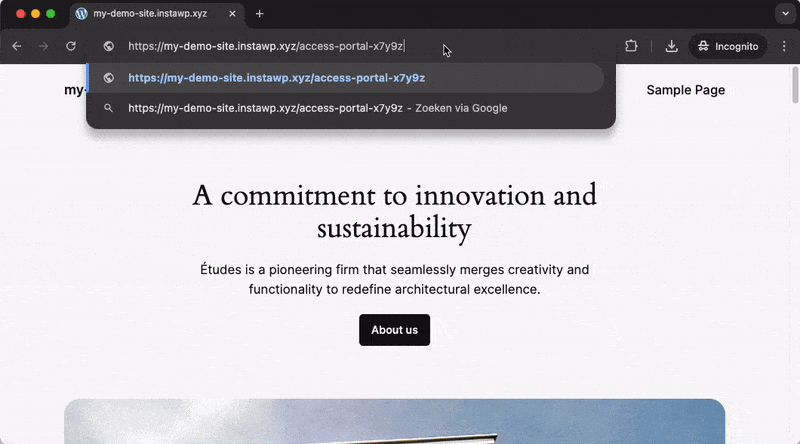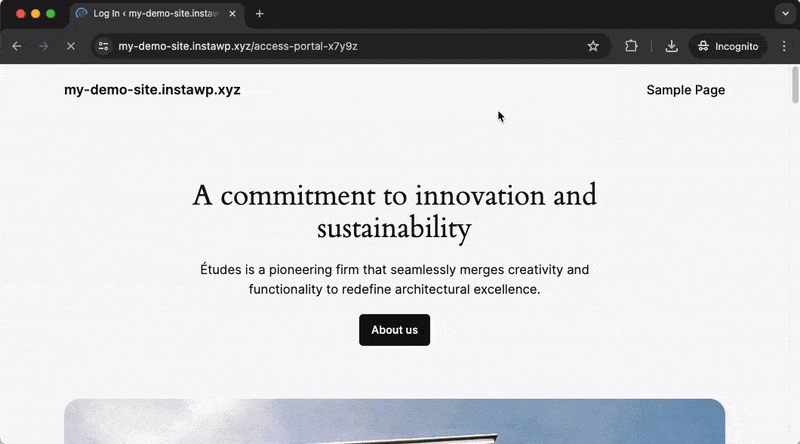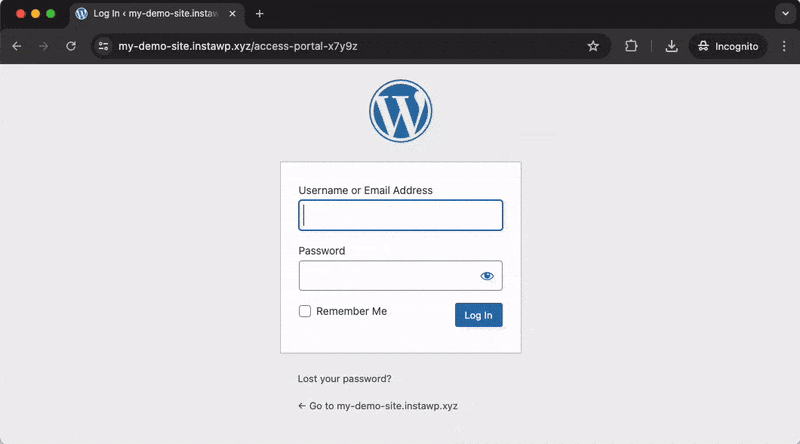
Instead, when using the Custom Login URL that has been configured in Really Simple Security, you will be redirected to the correct login page.
Note: This feature can deter casual attackers and reduce the effectiveness of automated threats and bots, however, it does not guarantee complete protection against a determined attacker who might be able to discover the new login URL through other means.
Disable User Enumeration
This functionality (located under Settings -> Hardening -> Basic) prevents attackers from easily discovering account usernames through Author ID pages. A detailed explanation and demonstration of this setting is available here:
https://really-simple-ssl.com/hardening-your-websites-security/#basic-user-enumeration
Block ‘admin’ Username
Renames any accounts with the ‘admin‘ username (a common target for hackers) and prevents the creation of new users with that username (Settings -> Hardening -> Basic).
https://really-simple-ssl.com/hardening-your-websites-security/#basic-block-admin-username
Block User Registrations with identical Login and Display names:
Enforces a separation between Login usernames and Display names, to prevent attackers from obtaining the Login Username of accounts on your website by simply checking their publicly available Display Name (Settings -> Hardening -> Basic).
https://really-simple-ssl.com/hardening-your-websites-security/#basic-login-display-name
