WordPress is a free and open-source content management system (CMS) that leads the global market as the most used CMS. According to W3Techs, about ~43% of all websites run on WordPress; which includes those of some of the largest companies in the world. It boasts a large community of users and developers who actively contribute to the project, greatly benefiting the platform’s reliability and security.
Still, you might occasionally hear that WordPress is perceived as a target for hackers, which leads some people to question the platform’s security. This perception can largely be attributed to WordPress consistent popularity over the years. WordPress being the most used CMS simply makes it an attractive target for attackers, rather than there being any inherent flaws in the platform itself. In fact, WordPress Core is considered highly secure for several reasons:
- Free and open-source: WordPress’s open-source nature is an important reason for the platform being as secure as it is. WordPress benefits from a large community of users and developers who actively contribute to the project, which significantly benefits its reliability and security.
- Closed-source/proprietary software is likely to contain an equal number of vulnerabilities (potentially even more), but in those cases, the discovery process is more obscured. It often takes longer for vulnerabilities to be identified and resolved due to the limited number of eyes on the code.
- Frequent security updates: The WordPress Core team regularly releases updates to address security vulnerabilities, and improve the platform’s overall security. With countless developers around the world being able to examine the platform’s openly available code, vulnerabilities are often identified and fixed quickly.
- Vulnerability reports for WordPress are publicly shared, which shows the community’s commitment to identify and patch vulnerabilities as soon as possible. Besides, vulnerability reports are typically only published after the issues have already been patched.
However, even though WordPress Core provides a very secure foundation, the security of a WordPress website ultimately depends on how it’s used and maintained. Many security issues arise from improper usage, rather than flaws in the core software itself.
Website Hosting and Security
Your hosting environment plays a crucial role in your website’s overall security. It’s important to recognize where the responsibility of your hosting provider ends and yours begins. Many hosts use standard security configurations to protect their infrastructure, but those measures might not be sufficient to detect and prevent website-specific malware infections.
In general, we recommend considering the following aspects when looking for a trustworthy web hosting provider:
- Up-to-date software: Ensure that your host provides you with the recent, stable versions of all server software.
- PHP version: Use the latest supported PHP version. Avoid themes or plugins that require you to use an older PHP version – as using outdated PHP versions versions can expose you to security vulnerabilities and bugs that have already been fixed in more recent versions of PHP.
- Proper TLS configuration: Ensure that your host uses secure TLS versions and cipher suites.
Really Simple Security can help you verify these aspects of your hosting security. In the Really Simple Security Dashboard, you will find an SSL test to verify your server’s SSL/TLS configuration which provides feedback about the configuration if any issues are detected.
Plugins, Themes and WordPress Security
WordPress Core is considered highly secure on it’s own, but most WordPress websites also use various third-party plugins and themes to extend WordPress’ standard functionality.
And with every third-party plugin or theme that you install on your WordPress site, it simply means that you’re trusting additional code from a third-party developer, thereby also increasing the risk of introducing a security issue. Vulnerabilities in WordPress plugins and themes are discovered and disclosed on a regular basis, and hackers actively scan for websites using vulnerable versions of software (such as plugins and themes) that they can exploit.
Keeping your plugins up-to-date is therefore essential, but even with regular updates: you would still have to be aware that your site was exposed to a vulnerability and how severe that specific vulnerability is, to fully understand the impact it has on your site. Vulnerability Detection in Really Simple Security provides you with all of that information.
Selecting safe and trustworthy plugins
Aside from keeping your software up-to-date, it is a good practice to be selective with any new plugins (or themes) that you install on your website. Wherever possible, we recommend sticking to plugins that are available in the official WordPress.org Plugin Directory. Any new plugins that are submitted to this directory are reviewed by the Plugin Review Team before being approved; which ensures that a certain standard of quality and secure coding practices have been followed.
In addition, each plugin in the Plugin Directory contains an overview with important details about that plugin, allowing you to determine how trustworthy a plugin is. All of this information can help you determine whether a plugin can reasonably be trusted. 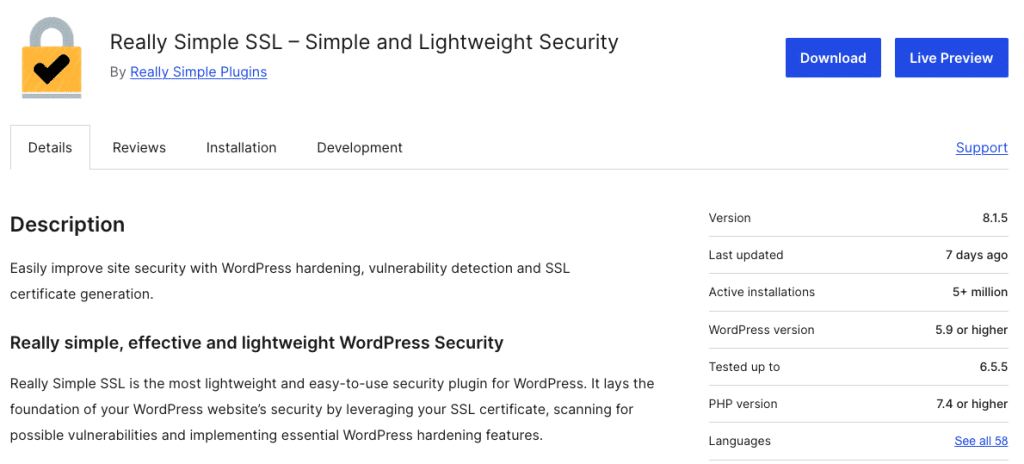
To help you make informed decisions when selecting plugins, we have highlighted some of the most valuable indicators below:
- Active installations: A high number of active installations generally indicates that a plugin is widely used (and trusted).
- Last updated date: The date when the plugin was last updated indicates whether it’s developer is actively maintaining the plugin. This makes it much more likely that the developer actively addresses security vulnerabilities, and ensures that their plugin is compatible with the latest WordPress and PHP versions.
- Reviews and ratings: Read through user reviews and ratings to learn about other users’ experiences with a certain plugin.
- Support: Each plugin on WordPress.org has a Support Forum where users can request assistance. You can browse through the Support Forum of a specific plugin to check if users requesting support receive timely answers from the plugin’s developer.
Vulnerability Detection & Measures
Ensuring that you only install trustworthy plugins from reputable authors plays an important role in keeping your website safe. However, even with these precautions, there is no 100% guarantee that a plugin won’t introduce any security vulnerabilities.
Really Simple Security offers increased protection against vulnerabilities with Vulnerability Detection, which notifies you if any known vulnerabilities are detected in version(s) of plugins, themes and WordPress Core on your site. The plugin provides an overview of all vulnerable components where you can update them directly, and notifies the Site Administrator by email if any vulnerabilities are detected.
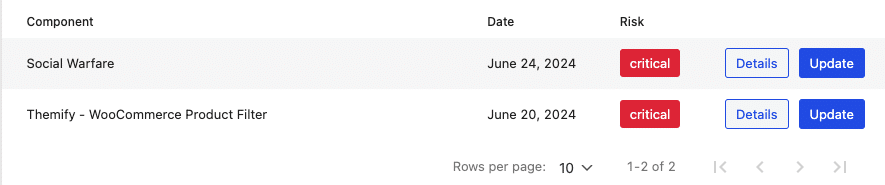
You can additionally enable the “Feedback in plugin overview” setting (under Vulnerabilities -> Configuration -> Notifications) to display vulnerable plugins directly in the Installed Plugins overview, alongside the risk level of the vulnerability.
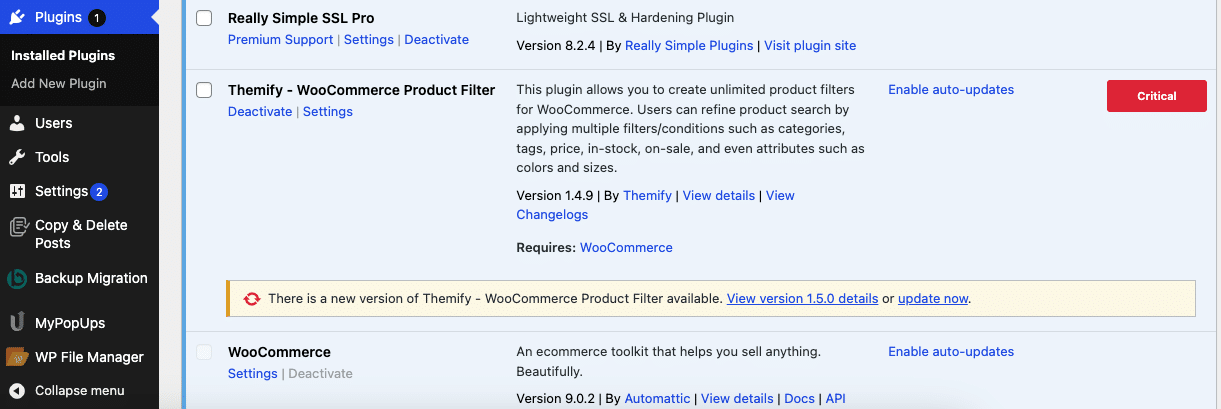
The Pro plugin can automatically take the necessary measures when a vulnerability is discovered on your site; such as force updating the vulnerable plugin, or quarantining the plugin entirely (e.g. if force updating fails, or a patched version of the vulnerable plugin is not available). You can configure which measure(s) should be taken based on the risk level of a vulnerability.
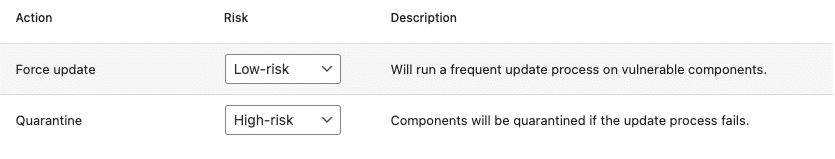
By ensuring that you are properly informed about the presence of vulnerable components of your site, and taking quick action if a component on your site (such as a plugin or theme) does happen to contain security vulnerabilities; you are a step ahead of malicious actors attempting to exploit these to gain unauthorized access to your site.
Login & Authentication: Securing User Accounts and Passwords
Protecting your site against vulnerabilities is crucial, but ensuring that user accounts are protected is equally important for the security of your website. If a privileged Account on your WordPress website (such as an Administrator account) is compromised by an attacker, this would grant the attacker with Administrator level capabilities on your site.
Login Protection
As briefly mentioned above, it is possible for a WordPress website to get hacked even if there are no known vulnerabilities in any plugins or themes on the site.
This could involve an attacker successfully logging in to an Administrator account by trying previously ‘leaked’ passwords (e.g. obtained from the database of a previously breached website), or the Administrator’s local device might have been infected with malware, which resulted in their WordPress Admin credentials being stolen. To strengthen the authentication mechanism of your WordPress site, we recommend enabling the Login Protection features mentioned below.
Two-Factor Authentication
It is highly recommended to enable Two-Factor Authentication (2FA) and require your users (especially users with privileged access to the site, such as Administrators) to verify their identity with an additional step during the login process, besides just the username and password.
This ensures that even if the password of an account somehow ends up in the wrong hands, the attacker would still need the “second factor” to successfully log in to the site, such as a one-time password (TOTP) generated with an authenticator app (e.g. Google Authenticator) or a verification code sent via e-mail.
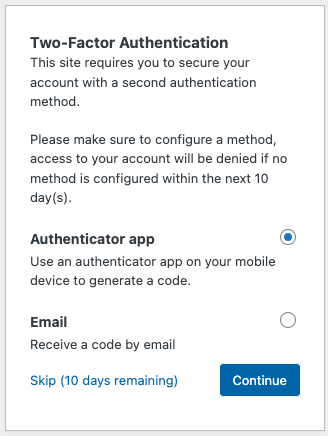
Our recommendation is to enforce Two-Factor Authentication with the TOTP method for all Administrators, as this generates verification codes on a separate device. We advise against allowing Administrator users to use E-mail verification as their 2FA method.
Detailed instructions on how to configure Two-Factor Authentication in Really Simple Security Pro are available in the article below:
Limit Login Attempts
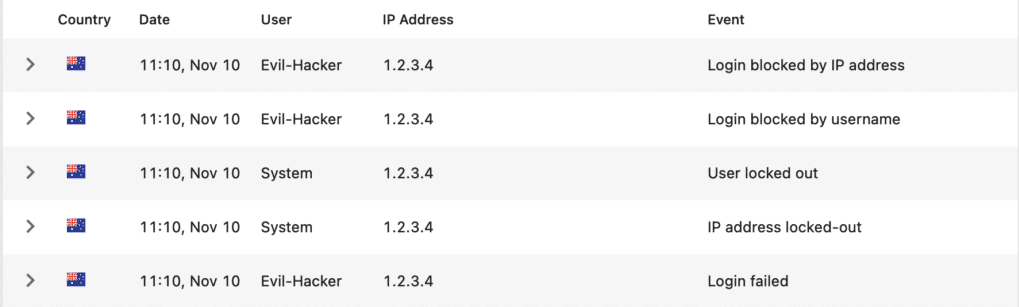
The Limit Login Attempts feature can be applied as further protection to the login mechanism of your site, which protects your site from unauthorized login attempts by automatically blocking repeated failed login attempts; and logging all activity on the login page in the Event Log.
Repeated login attempts with invalid credentials from specific IP addresses or users are blocked automatically, with a customizable lockout duration. It is also possible to create permanent blocklists. The Event Log provides you with an overview of activity on the login page, allowing you to quickly identify any suspicious behavior.
You can even block login attempts based on geographic location; to prevent certain countries (or entire continents) from logging in to your site altogether. Rest assured; this does not affect regular visitors on your website, it only affects login attempts.
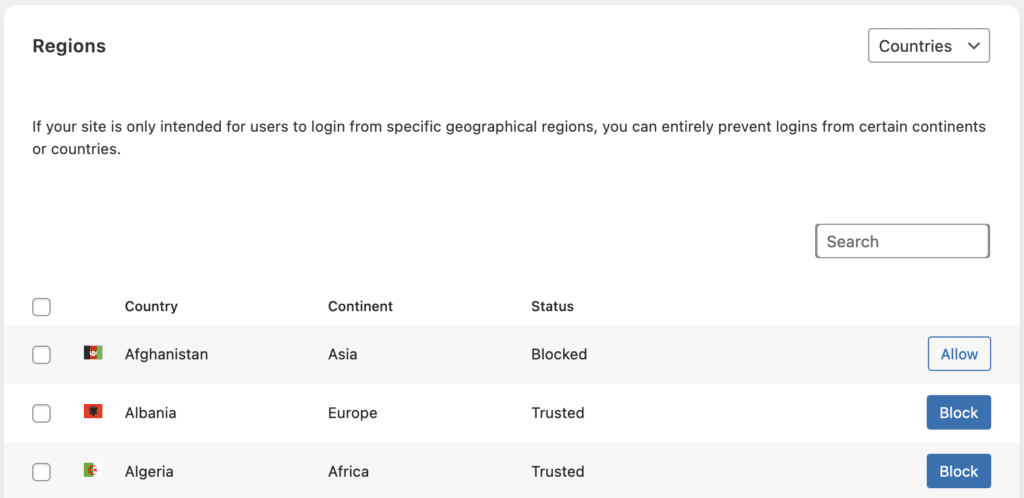
For a full overview of the Limit Login Attempts feature and how to configure it on your site, please refer to our earlier article about the feature:
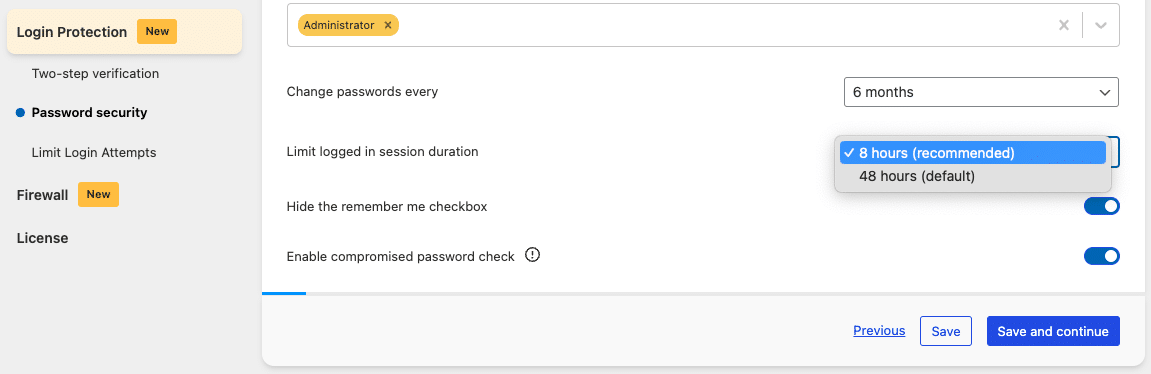
Password Security
Enforce strong passwords
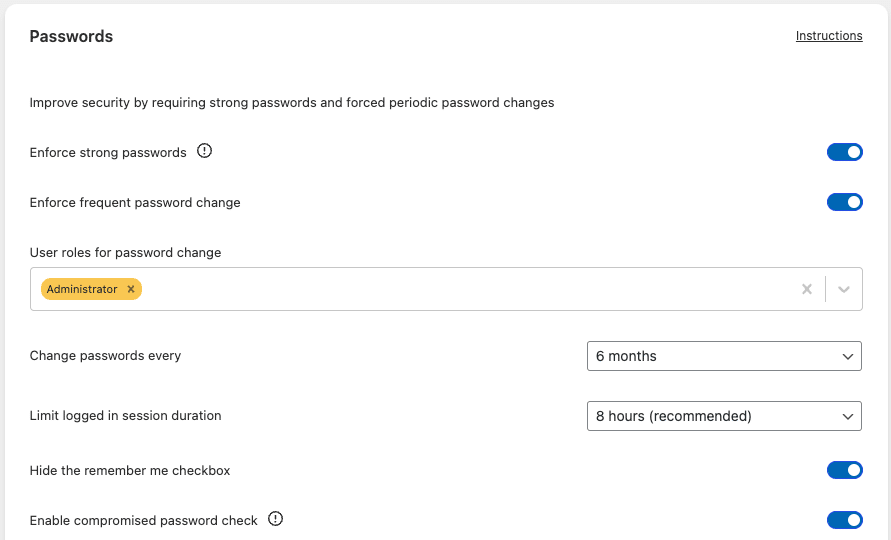
The “Enforce strong passwords” setting, located under Settings -> Login Protection -> Password Security, expands upon WordPress’ default password strength check by requiring users to configure a strong password for their account; they won’t be allowed to proceed with a password that does not meet the requirements.
Compromised password check
One of the most significant risks that impact the security of accounts on your WordPress website involves the use of passwords that had previously been compromised in data breaches.
Enable the “Compromised password check” setting to verify whether compromised credentials are being used during account creation (or modification), to check whether a password has previously appeared in any data breaches, by cross-referencing it with the Have I Been Pwned database. This prevents the password from being used if it was previously breached.
Enforce frequent password change
The “Enforce frequent password change” setting forces frequent password changes for all users, or for specific user roles (for example: to only apply this requirement for Administrators).
Combining these three settings ensures that all accounts on your WordPress site use frequently updated & sufficiently strong passwords that haven’t appeared in any previous data breaches, significantly reducing the risk of a successful brute force/credential stuffing attack.
Managing Session Duration
After successfully logging in to your WordPress site, you will receive valid session/authentication cookies. These cookies grant you access to the site without the need for re-authentication (until the authentication cookies expire).
However, if the authentication cookies of a user are somehow obtained by an attacker (for example, the user’s own device was infected with malware), this could enable the attacker to use or insert these stolen auth cookies into a new session; and the attacker would be authenticated as that user until their authentication token expires. Such types of attacks are commonly referred to as session hijacking or ‘pass-the-cookie’ attacks.
To limit the window of opportunity for an attacker to exploit stolen authentication cookies, we recommend setting the “Let login cookie expire after” option to 8 hours (Settings -> Login Protection -> Password Security). These changes will take effect after logging out & logging back in to your WordPress Account. Note that the login expiration would still be set to 14 days if the “Remember Me” checkbox was enabled. To prevent this, enable the “Hide the Remember Me checkbox” setting as well, which removes that option from the login page.
Hardening
There are certain features in WordPress that potentially pose a security risk if they are not configured appropriately. Really Simple Security allows you to easily activate additional security measures to either disable or enforce stricter limits on the use of these functionalities, to prevent them from potentially being abused by an attacker.
You will find all of the available Hardening features explained in our dedicated article on the subject: https://really-simple-ssl.com/hardening-your-websites-security/
