We recently introduced vulnerability detection in Really Simple SSL and have been working on a database of vulnerabilities sourced from the open WordPress Vulnerability Database API project (https://www.wpvulnerability.com) since the beginning of 2023.
We have been monitoring WordPress plugin and Theme vulnerabilities for years and have seen an increase in reported vulnerabilities yearly. Having access to detailed information in our own database enabled us to look closer into the details and numbers.
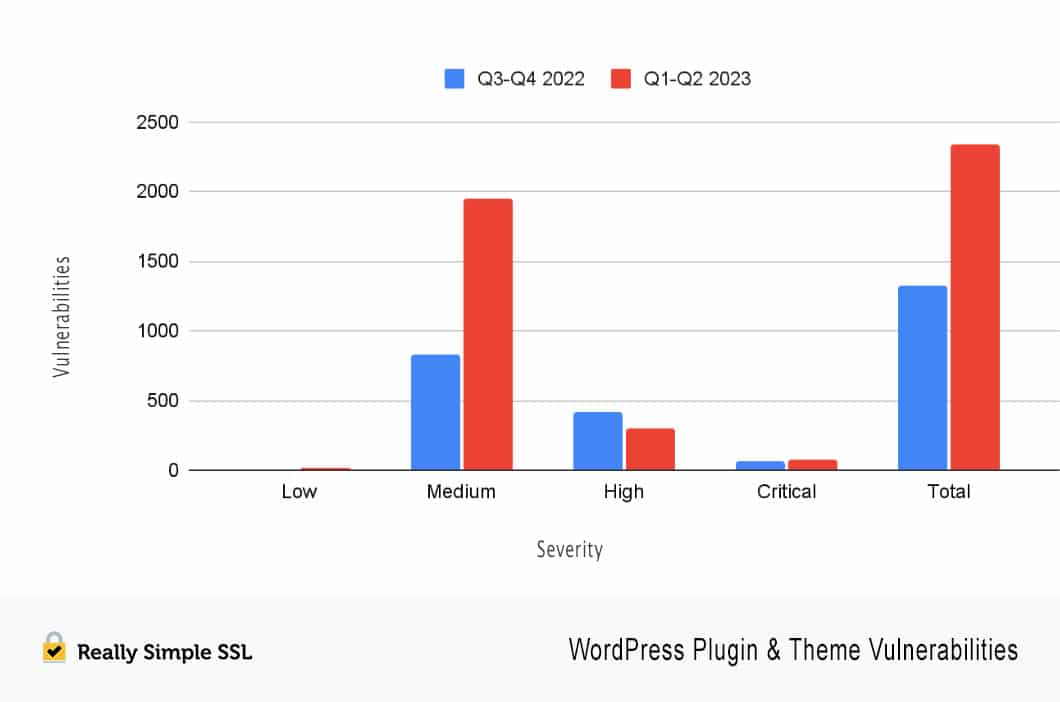
We were surprised to find the number of reported vulnerabilities had almost doubled in the first 6 months of 2023 compared to the last 6 months of 2022.
Peter Tak - Security Consultant Really Simple Plugins
Is WordPress Plugin & Theme security failing?
Are developers suddenly lapsing into implementing security best practices? Is there a significant increase in hacked WordPress sites? Not according to our own research and feedback from our customers.
Many WordPress sites are still getting hacked every day, but not twice as much as last year, as far as we can determine.
Then what’s going on here? As you can see in the chart above, there is a considerable increase in medium-severity vulnerabilities. On the other hand there is a 25% decrease in high-severity vulnerabilities compared to last year. More vulnerabilities are being found, but that does not mean plugins or themes are getting less secure overall.
What is happening is that there are several programs for reporting vulnerabilities in WordPress plugins & themes, and some of these programs even pay a reward for every qualifying vulnerability. This has resulted in security researchers actively searching the repository for vulnerabilities in search of rewards and recognition. This is a good thing, even when it results in many relatively low-impact vulnerabilities being reported.
Not all vulnerabilities are the same
For example, we had a vulnerability reported in one of our plugins, where a logged-in administrator could be tricked into clicking on a hyperlink by the attacker, which would result in a restart of a tour of plugin features.
This is a vulnerability because actions that were not intended can be performed but it does not pose any real-world risk. We found many more examples of trivial issues reported as vulnerabilities with no real-world exploitation scenarios that could benefit an attacker. Which is great; it forces developers to pay closer attention to what they are doing and write secure code everywhere. That will enhance security over the entire WordPress plugin and theme ecosystem.
Conclusion
Even though there is a massive increase in vulnerabilities reported, we do not see a deterioration in the security of WordPress plugins and themes. There have been and will always be vulnerabilities in software code, and the fact that they are found more often and faster than before is a good thing because they can be fixed before they are abused.
Most of the time, as soon as a vulnerability is found by “the good guys” they will inform the developer, and a fix will be made and distributed. Usually, when the developer does not respond, the researcher will notify the WordPress plugin team. In this case, the WordPress plugin team may choose to close a plugin (basically removing the ability to download from wordpress.org). In extreme cases (plugins with lots of active installs and high risk), they may even create a fix and force distribute an update for all users.
The downside is that the “bad guys” also monitor these reports and will try to exploit vulnerabilities as soon as they are published. Even though a lot of the increase in vulnerabilities found can be categorized as low risk, multiple new high-risk vulnerabilities are published weekly.
Update Update Update..,
In light of this it has become more important than ever to quickly update when a security issue has been fixed. The problem is that a some of the reported vulnerabilities are not fixed at all.
According to our data there are currently 428 plugins and 72 themes in the repository with an open security vulnerability. In most cases these are vulnerabilities with limited risks for site owners and users. Further detailed analysis of these vulnerabilities shows that 84% of plugins & themes in the wordpress.org repository with an open security vulnerability have not been updated in the last 6 months.
Peter Tak - Security Consultant Really Simple Plugins
What should I do?
To ensure you are aware of vulnerabilities in your installed plugins and themes, you should use a solution that scans your site and informs you about them. Really Simple SSL can do this for you and even offers to force updates or quarantine a plugin when high-risk vulnerabilities are found.
Addressing security vulnerabilities in WordPress plugins & themes requires a collective effort from plugin developers, the wordpress.org plugin team, website administrators, and the WordPress community as a whole. Regular updates, security audits, vulnerability disclosures, education, and awareness campaigns can help mitigate these risks and ensure a safer WordPress ecosystem.

