Re-using passwords that have previously been breached poses a significant security risk to the accounts on your WordPress website. It might allow a hacker to perform a successful credential stuffing attack, whereby they attempt using previously breached usernames and passwords to gain access to accounts on various websites.
Really Simple Security now offers a powerful compromised password check feature to protect you against these types of attacks. This setting prevents users from using passwords that had previously been exposed in data breaches. To enable this functionality, navigate to SSL & Security -> Settings -> Login Protection -> Password Security and activate the “Compromised password check” slider.
How does it work?
This feature verifies whether a password has previously appeared in a data breach by cross-referencing the password with the HaveIBeenPwned database, and prevents the password from being applied if this is the case. This requirement applies to new account registrations as well as password changes for existing accounts.
If a user attempts to set a password that was found in one or multiple data breaches, they are prevented from using that insecure password and will receive the following message to indicate this:
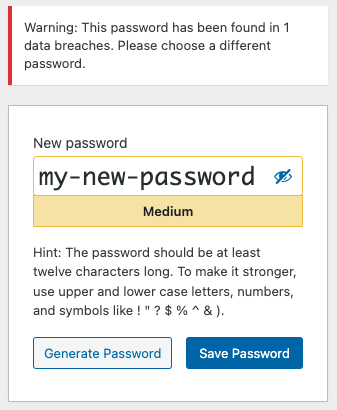
Frequently Asked Questions
Will this affect my existing users?
Only when they attempt to change their password.
We therefore recommend enabling the “Enforce frequent password change” feature alongside the Password Security Scan, to enforce frequent password changes for all of the user accounts on your site. When a user has to reset their password, they will now be required to select a password that meets the new requirements.
Are passwords being sent to a third-party service when I try to register an account or change my password?
No, the full password is never transmitted to any third-party service. We use a highly secure method (read more) to check if the password has appeared in known data breaches.
- We take only the first 5 characters of a specially encoded version of your password (called a “hash”).
- This small piece of information is compared with HaveIBeenPwned’s database of known breached passwords.
- The database returns a list of partial matches.
- Our system checks if the password matches any items in this database, all without ever sending the actual password anywhere.
This process ensures that your password remains private and secure, whilst still allowing us to check if it has been compromised in past data breaches.
