HSTS (HTTP Strict Transport Security) is available in Really Simple SSL pro, and most people just activate it. But it’s good to know why you need it.
When you have an SSL certificate on your domain, anyone can still use your site over the http (insecure). The simplest solution is to add a redirect. That’s one of the features of Really Simple SSL: it adds a redirect to your site that forces it over SSL.
But what if someone pretends to be your site? This can happen anywhere, and is quite simple to achieve: a user types in domain.com, but malicious software directs the request to a site pretending to be domain.com. Now the user is open to attacks.
HSTS: prevent http requests to your domain
That’s where HSTS, or HTTP Strict Transport Security comes into play. When this header is set on your domain, a browser will perform all requests to your site over https from then on.
So, in the case where a hacker is redirecting this user to a fake “domain.com”, the browser remembers to use SSL because of the HSTS, and it requests the secure site. But this doesn’t exist: no SSL certificate was authorized for the hacker’s fake site. As the browser needs to visit your site first to see this header, this will be active only after the first visit.
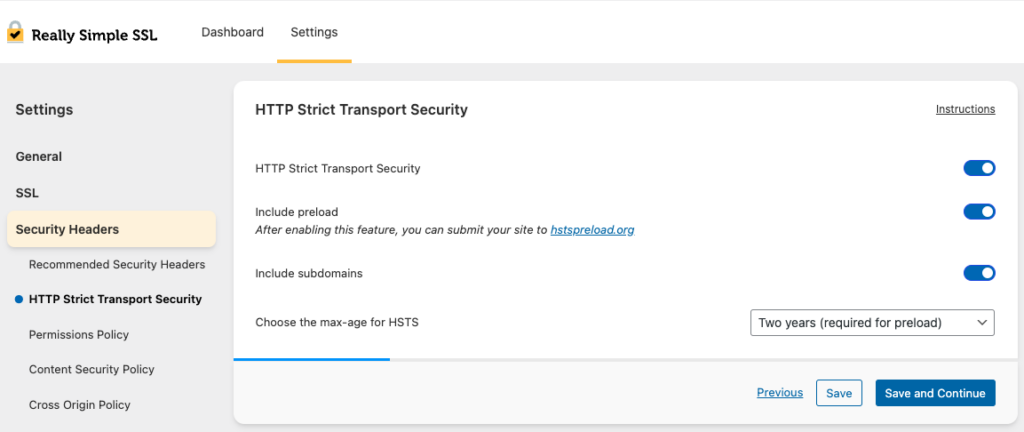
To enable HSTS, you can simply enable the setting in Really Simple SSL Pro which is located under Settings -> SSL & Security -> “Settings” in the top menu bar -> Security Headers -> HTTP Strict Transport Security.
HSTS Preload list: Preventing http requests on the first visit
As HSTS is only enforced after the browser has visited your site once, this is a vulnerability: when the user hasn’t visited your site before, HSTS won’t be set, so at that point the visitor can still request the site over http.
There is a solution: the HSTS Preload list (https://hstspreload.org/). This is a list of HSTS domains that is preloaded in browsers. If you’re on the list, the browser will know that it should only load your site over https, even before it ever requests your site with the HSTS header set.
If you enable HSTS and wish to submit your site to the preload list, make sure to additionally enable the Include Preload, Include Subdomains options, and set the max-age for HSTS to two years.
Be careful before submitting your site to the HSTS Preload list though. It means that all subdomains (e.g. sub.domain.com) will be forced over https as well. Removal from the preload list is very difficult, and might not propagate very fast. So even when you’re removed, your site may still be included in the list for months.

