If the login credentials of accounts on your WordPress sites are compromised, this could result in your site getting hacked. The Password Security features in Really Simple SSL aim to strengthen the protection of WordPress accounts on your website. We will explain each of these features below, and how they can help you improve the security of user accounts.
Securing User Accounts and Passwords
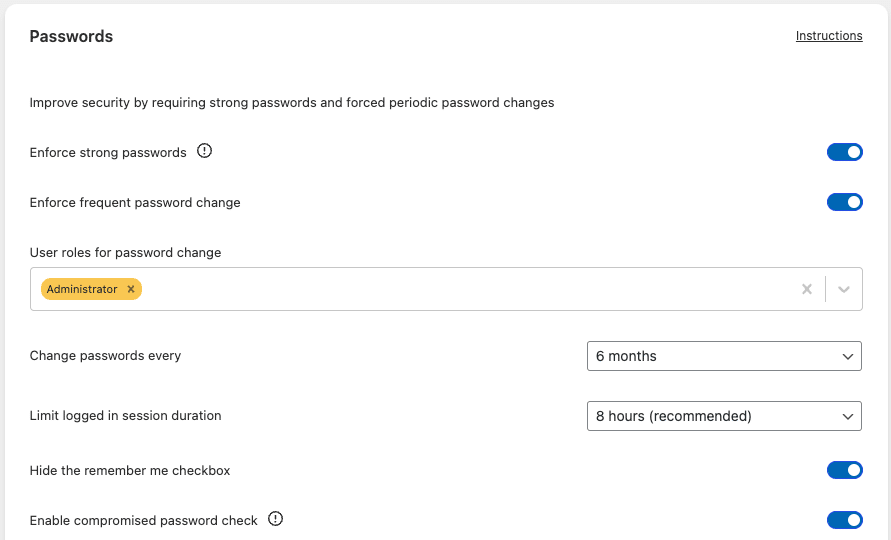
- Activating the “Enforce strong passwords” setting enhances WordPress’ default password strength check (for all new user registrations); this removes the possibility for users to configure weak, and medium passwords for their account.
- Enabling the “Enforce frequent password change” setting forces frequent password changes for all users, or just for selected user roles (e.g. Administrators), to make sure that all of the accounts on your WordPress site are using sufficiently strong passwords.
- Users that have to change their password due to this setting, will receive an email to inform them that their password will expire in 7 days. After 7 days they will be notified that their account is locked, and that they will need to reset their password before logging in again. If you enabled the “Enforce strong passwords” setting as well, these users are now required to select a password that conforms to the password strength check.
- Enabling the “Compromised password check” setting verifies whether a password has previously appeared in any data breaches, by cross-referencing it with the Have I Been Pwned database, and prevents the password change from being applied if it appeared in any previous data breaches.
Controlling User Sessions
After a successful login to your WordPress site, you will receive valid session/auth cookies which allow you to access the site without the need for re-authentication (until they expire). In other words, these cookies can be seen as ‘digital keys’ which allow you to access the site.
However, if the session cookies of a user are stolen by an attacker (for example; due to the user’s local device being infected with malware): the attacker might be able to perform a session hijacking or “pass the cookie” attack, whereby they use browser tools or modified web requests to insert the stolen auth cookie into a new session; and the attacker would then be authenticated as that user until the token expires.
To limit the window of opportunity for an attacker to exploit this, we recommend setting the “Limit logged in session duration” option to 8 hours.
Please take note of the following details with regards to the login cookie expiration setting:
- Any changes to the auth cookie expiration will only start to take effect after logging out & logging back in to your WordPress Account
- The expiration of the cookie would still be set to the default value (14 days) if the “Remember Me” checkbox was ticked during the log-in. To prevent this you can enable the “Hide the Remember Me checkbox” option as well, which removes the Remember Me option from the login page.